The story of the Linksys Wireless-G Router (model WRT54G) and how you can turn a $60 router into a $600 router is a little bit CSI and a little bit Freaks & Geeks. It’s also the story of how the open source movement can produce a win-win scenario for both consumers and commercial vendors. What’s especially exciting is that tricking out this router doesn’t require any eBay sleuthing or other hunt for some off-the-wall piece of hardware. Instead, grab it off-the-shelf. The WRT54G is stacked high in every Best Buy and Circuit City across the country and, of course, most online retailers — Amazon.com sells it for $55. It’s ubiquitous and, some would say, a diamond in the rough. Or a wolf in sheep’s clothing.While routers used to be the domain of networking specialists, they’ve gone mainstream along with residential broadband. Commodity routers can be had for as little as – well, "free after rebate” in some cases, and often not much more. To keep them cheap, consumer-grade vendors like Linksys repackage designs from OEM vendors rather than design the hardware and software in-house.The tradeoff for these sub-$100 routers can be reliability, particularly in the coding of the firmware – the software “brain” that controls the router’s functions.
Consumer-grade firmware may be buggy, and may be limited in functionality compared to commercial-grade routers designed for business such as those made by Cisco and SonicWall. The WRT54G was released in 2003 in anticipation of the 802.11g standard, with its theoretical maximum bandwidth of 54Mbps compared to 802.11b’s 11Mbps. In many respects the WRT54G is a typical wireless router – it accepts an incoming broadband link such as cable or DSL and shares it between its built-in four-port Ethernet switch and antennae for broadcasting the signal to wireless clients.In June 2003 some folks on the Linux Kernel Mailing List sniffed around the WRT54G and found that its firmware was based on Linux components. Because Linux is released under the GNU General Public License, or GPL, the terms of the license obliged Linksys to make available the source code to the WRT54G firmware.
As most router firmware is proprietary code, vendors have no such obligation. It remains unclear whether Linksys was aware of the WRT54G’s Linux lineage, and its associated source requirements, at the time they released the router. But ultimately, under outside pressure to deliver on their legal obligation under the GPL, Linksys open sourced the WRT54G firmware in July 2003. With the code in hand, developers learned exactly how to talk to the hardware inside and how to code any features the hardware could support. It has spawning a handful of open source firmware projects for the WRT54G that extend its capabilities, and reliability, far beyond what is expected from a cheap consumer-grade router. Feature-Packed FirmwaresSo the Linksys WRT54G can be loaded with replacement firmware with exciting new features. Which raises the question – like what?Of course, you can expect most replacement firmware to support the same basic functions Linksys provides out of the box for this wireless router. Often these features will be more stable, in cases where Linksys’ bugs have been fixed by other developers. But that’s not what makes open source firmware so exciting.
The real deal is what the WRT54G can do, with the right replacement firmware, that you’d only expect to find on a commercial-grade router costing several times as much.You could use the WRT54G as a repeater or a bridge. Create a wireless distribution system (WDS) or a mesh network. Run a VPN server. Or a VoIP server. Or a managed hotspot with a RADIUS server. Manage bandwidth use per protocol. Control traffic shaping. Support IPv6. Boost antenna power. Remotely access router logs. Operate the router as a miniature low-power PC, running a variety of Linux applications. That’s just the short list. Some firmware offerings support a wide range of these features while others are more tailored to specific router applications. Some sport friendlier configuration interfaces while some are command-line driven. And because these firmware files descend from Linksys’ open-source progenitor, they are freely available. The important caveat, of course, is that Linksys will not support alternative firmware, only their own official version. Should you run into a problem with replacement firmware, or wind up disabling your router (which is rare but possible – stay tuned), you’ll be on your own.
If you already own a WRT54G and it performs just the way you need it to, mucking around with replacement firmware might just break something that didn’t need fixing.On the other hand, if adding enterprise features to a $60 router sounds worth the minimal risk, you don’t need any special hacker skills to get there. If you’ve already setup an off-the-shelf router before, replacing the WRT54G’s stock firmware with a feature-laden substitute is well within reach. Choose Your FirmwareBesides Linksys’ own official firmware, there are more than a dozen varieties of firmware replacements available for the WRT54G. The most popular are named Alchemy and Talisman, released by a company called Sveasoft, and another named DD-WRT, by a guy named BrainSlayer. Sveasoft was one of the first developers of a WRT54G firmware based on Linksys’ open source version. Many branches in the firmware family tree, including DD-WRT, are themselves based on Sveasoft’s early modification. Buffeted by the success and enthusiasm generated by their firmware offerings, Sveasoft chose to build a business model around their subsequent releases. Because of the GPL roots of the original Linksys firmware, Sveasoft cannot prevent distribution of their own modifications. As a workaround, they’ve chosen to implement a membership fee of $20 per year to access the Sveasoft “community,” wherein support and new releases are made available. Some in the open source community object to the “wall” Sveasoft has built around its free firmware, and take it upon themselves to release Sveasoft’s work into the public.Infighting aside, Sveasoft’s older Alchemy and newer Talisman firmware are popular and widely available.
BrainSlayer’s DD-WRT is free of the Sveasoft culture war, and is itself an extremely powerful and actively maintained firmware.Numerous other, often more specialized, firmware is also available for the WRT54G. Service provider Earthlink has released its own firmware which supports the future-proof IPv6 protocol (along with IPv4 backward compatibility). Sputnik, a vendor for large scale WiFi business networks, has even released firmware so WRT54G can be used in managing Sputnik-based hotspot deployments. Other online sources for firmware include LinksysInfo and WRT54G.net. But for most of us, the Sveasoft and DD-WRT firmwares are the most feature-rich and easiest to install and configure.In the two years since Linksys originally released the WRT54G firmware, whether by design or not, this affordable, common router has become not just a playground for hobbyists, but an open platform for commercial business as well.
Flash Your FirmwareOver the years Linksys has released several hardware revisions of the WRT54G, from 1.0 to 5.0 and several point releases in between. What version WRT54G router you have can be determined from its serial number as per charts widely available on the firmware community sites. The serial number is printed on the outside of the box.The reason this matters is because some versions of firmware work only with some versions of WRT54G. While the newest firmware releases for the major distributions such as Talisman and DD-WRT are compatible with most WRT54G revision, it is important to double check the particular release notes for a firmware version against the WRT54G version. A mismatch, although unlikely, is one way the router could be “bricked” – rendered unusable.With all that said and done, let’s imagine you’ve decided to try the latest version of DD-WRT – currently v23, which supports all current versions of the WRT54G, and its speed-enhanced sibling, the WRT54GS.
At the DD-WRT web site you’ll find three variations of the firmware: mini, standard, and VOIP. The DD-WRT wiki describes what is and is not included with each; suffice it to say, the standard variety is the most popular choice.WRT54G firmware come a file with the extension .bin. Regardless of which firmware you choose, be it a Sveasoft release, DD-WRT, or any other, ultimately you are going to have in your possession a .bin file which needs to be uploaded in to the router.
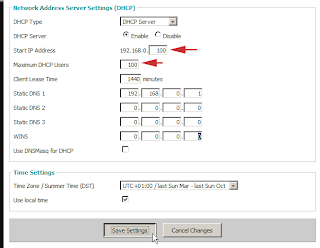
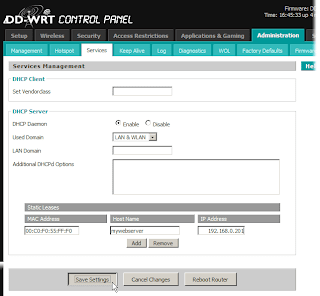
Flashing the new firmware is a painless process. If you’ve ever managed your router before, you know that it is configured through a Web browser open to the router’s LAN address – by default, this is 192.168.1.1 unless you’ve changed it. Linksys routers are protected by a login whose default is a blank username with the password admin.It takes only a few minutes to flash the router with a new firmware, but you must note these key steps.Connect your PC with the . bin file to the router via Ethernet cable. Do not try to flash the firmware through a wireless link, which could be unstable and lead to a brick.Reset your router’s current firmware to factory defaults. You can do this through the current firmware’s configuration pages – Administration/Factory Defaults/Yes/Save Settings. As an alternative, you can physically reset the factory defaults by pressing and holding the reset button on the back of the router for 30 seconds.Now you can flash the new firmware. Connect to the router’s configuration pages with your browser, and navigate to Administration/Firmware Upgrade.
Open the browse dialog to select your .bin firmware file.Once you start the firmware upgrade – do nothing! Whistle. Whittle. Have a pint1. Just don’t touch your computer or the router. Leave them alone for this intimate moment. Hacker interruptus will only produce a new baby brick.After a minute or so you’ll see the upgrade progress bar complete. The router will now reset itself, and assuming everything worked, you’ll see a new page with a button marked Continue.Wait at least two more minutes before clicking the Continue button. Sometimes the router presents the continue screen before it has truly cleaned up from its upgrade, and you’re better safe than sorry. Drink another pint2.Now click Continue.
You should be forwarded to the main configuration page for your router. In the case of DD-WRT, it looks much like Linksys’ own page, except with DD-WRT markings and a whole lot more features to explore.What if you didn’t make it this far? What if something terrible has happened, and the router did not come back to life? This is a rare but possible event. It is very unlikely if you’ve followed steps one through six. Your router may be bricked, which is somewhat like being dead, except with the possibility of resurrection.First, try to reset the router to factory defaults by pressing and holding the reset button on its rear for 30 seconds. When and if it relights, try to connect to it with your browser. You may be lucky and have a chance to start the process over again. There are several more tricks you can try to revive a bricked router, also known as recovering from a bad flash. In this case, you want to consult the WRT54G Revival Guide.
1 Something non-alcoholic, of course.
2 Try a refreshing mixture of Orangina and a twist of lime.
Now What?Your router has a new brain. From here you’ll want to explore the configuration pages and follow any guides or documentation available for the firmware you’ve installed. Unless you already know exactly which configuration pages you want to change, your best bet is to first identify your goals with the router. Do you want to use it to setup a WDS? Or configure it as a wireless client to connect a remote wired LAN to a remote wireless AP? There are myriad possible goals. Explore the user community for your firmware where there may already be detailed guides for configuring the router for the functionality you want, or experienced voices to help you troubleshoot. @abrar2009

 >
> >
>
















 Click the Advanced Settings tab. On the device 0 or device 1, a change Device Type None. Click OK.
Click the Advanced Settings tab. On the device 0 or device 1, a change Device Type None. Click OK.